HiddenVNC
♕Native stab, written in the C programming language, stab written from scratch.
System calls are used wherever possible, in other cases WinAPI is used, no third-party libraries are used or required.
♕ Work with bots occurs through a responsive Web interface, the panel allows you to work with several bots simultaneously.
Communication between bots and the server occurs via the HTTP protocol using its own encryption, bots do not know the real IP of the server to which they will connect, they will connect to "proxy domains", which increases survivability.
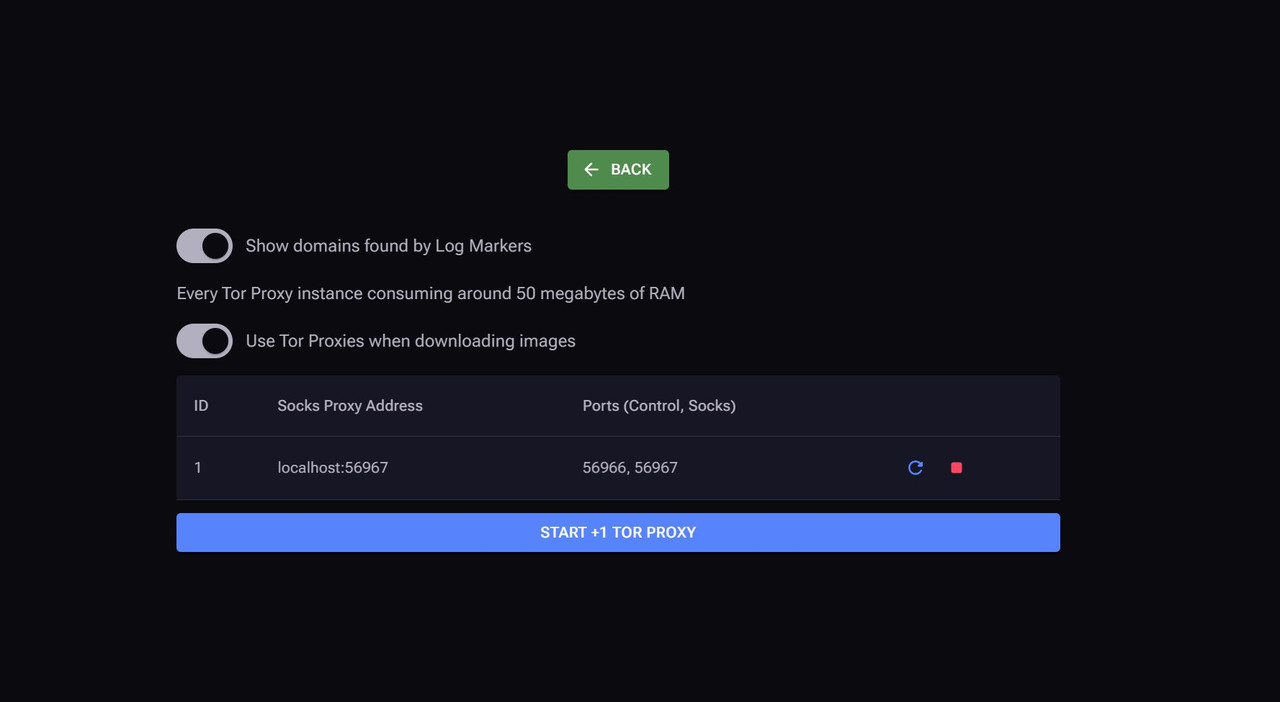
♕ Gasket system (proxy) - we do not show the IP where the connection from the bot to your server occurs, due to this, the survivability of the bot increases.
♕ Personal server - for each Spyware client, we set up a personal server, bots will connect to your server via gaskets.
♕ Convenient control panel in the Browser - the ability to manage several bots simultaneously from one or several accounts (teamwork), support for Light and Dark interface themes.
♕ At the moment, several modules have been created:
View and stop Windows processes
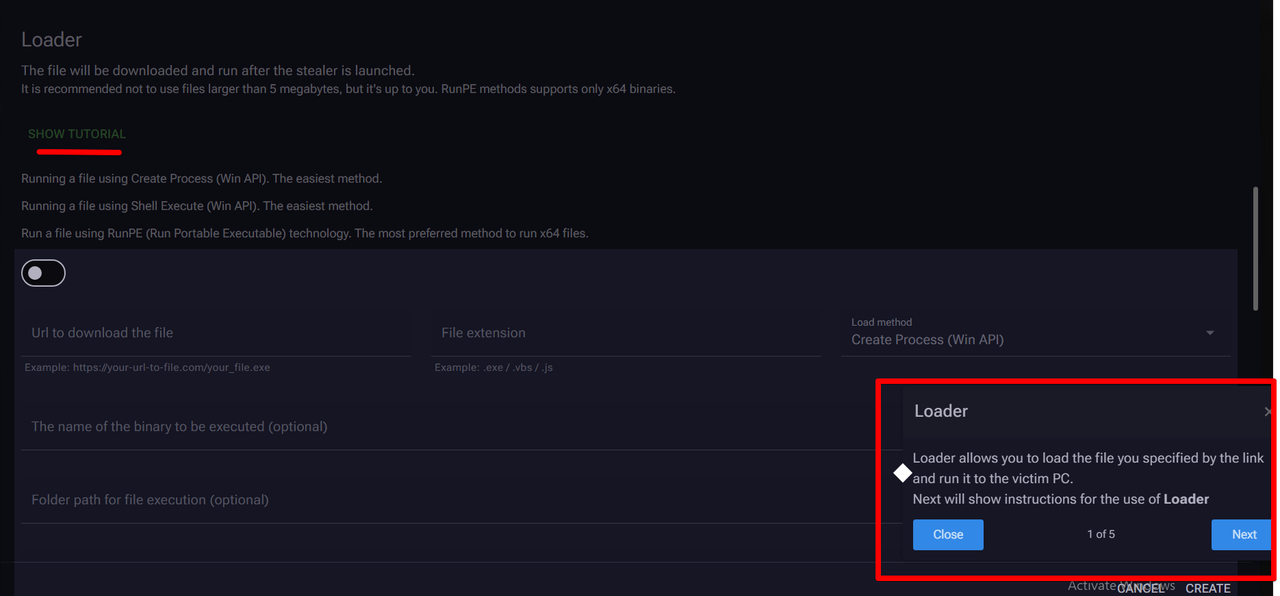
Loader: launch commands via Shell Execute for the bot
Download And Execute: download and run files for the bot, HTTP and HTTPS links are supported.
Mass deletion of bots
HVNC (Hidden VNC, Hidden session similar to VNC)
Hidden screen for controlling the victim's device allows you to work at a speed of up to 30 FPS (depending on their and your connection stability)
The same keyboard layout as the selected bot is available
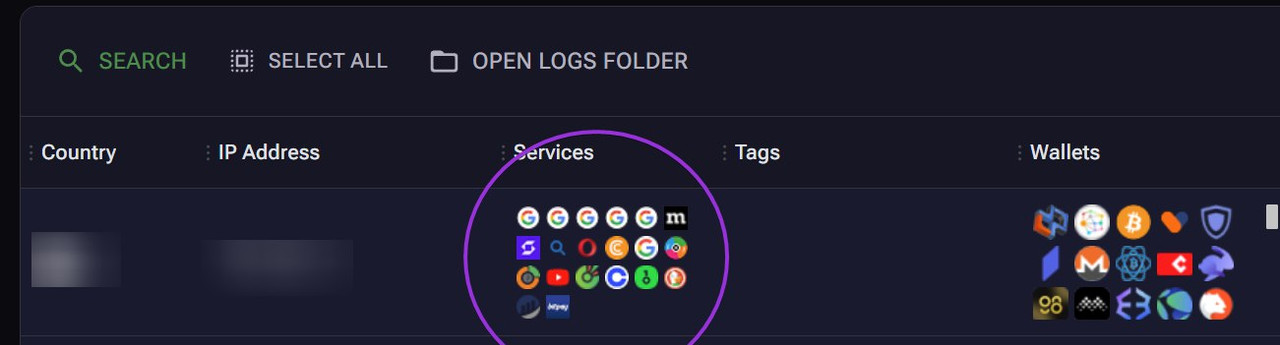
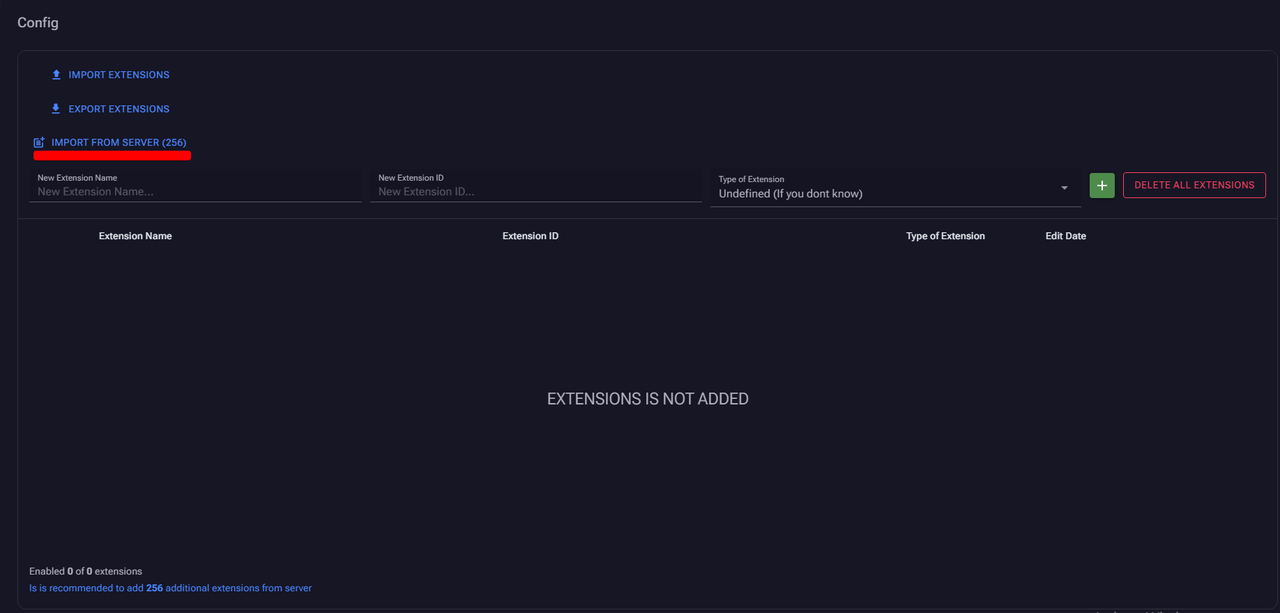
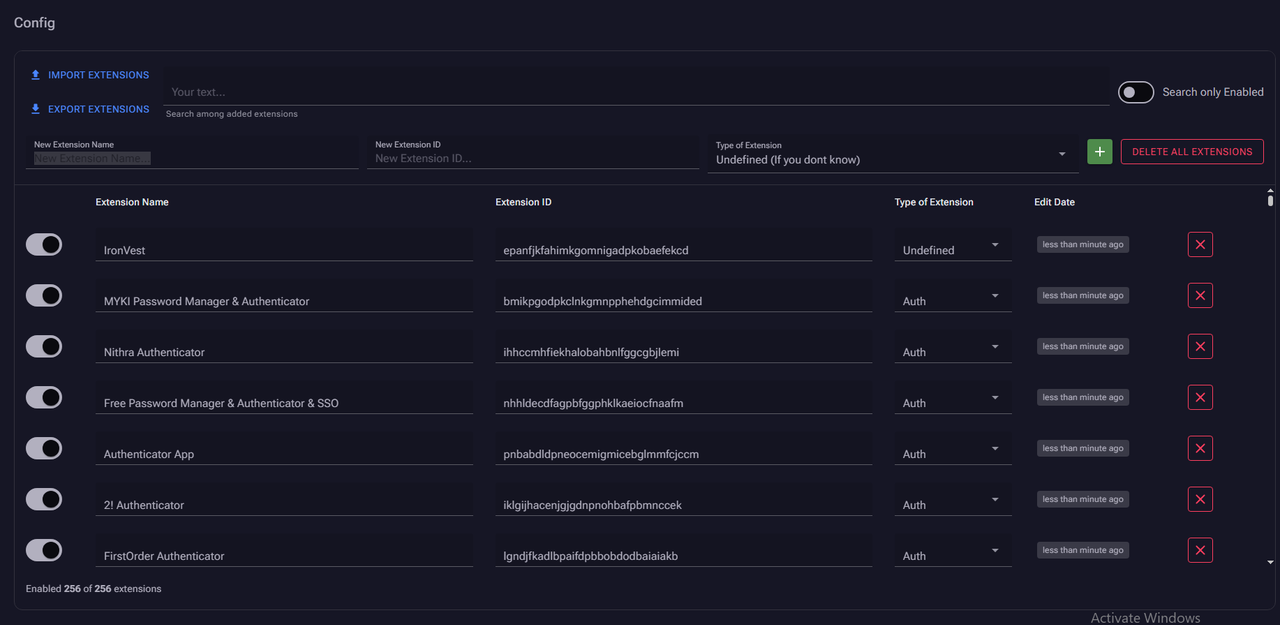
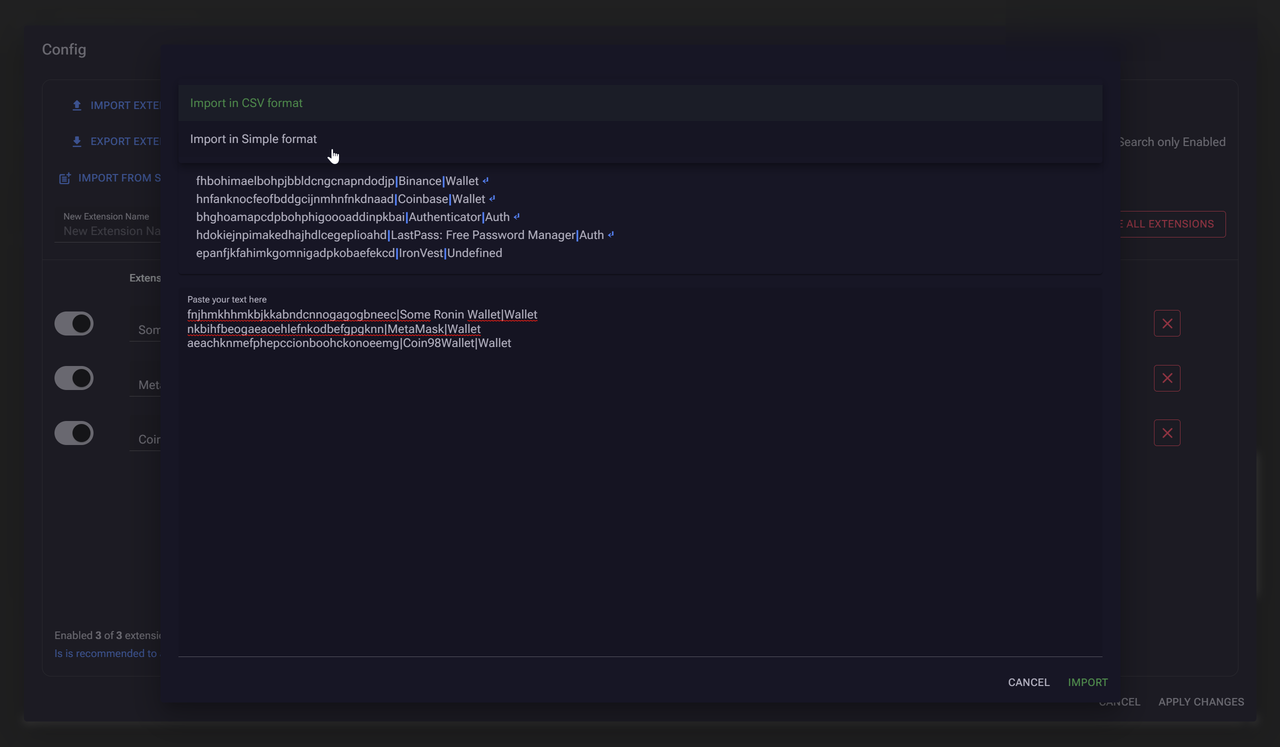
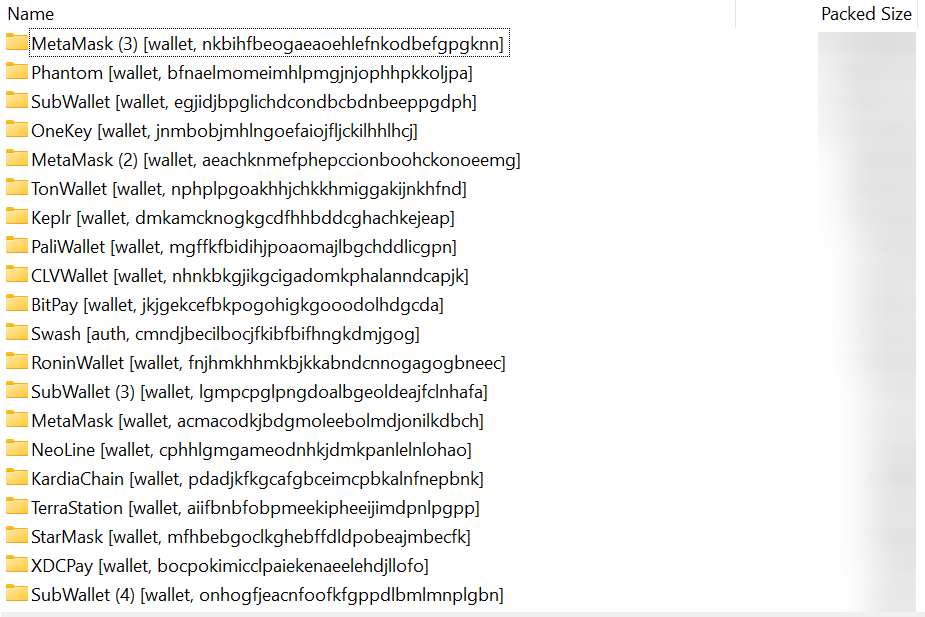
Clipper
- Clipper crypto wallet substitution, currently we support substitution
Bitcoin Legacy and P2SH Addresses
Bitcoin Bech32 Addresses
Monero (XMR) Standard addresses
Stellar (XLM)
Ripple (XRP)
Litecoin (Legacy) (LTC)
Litecoin (Bech32) (LTC)
Neocoin (NEO)
Bitcoin Cash (Legacy and New)
Dashcoin (DASH)
Dogecoin (DOGE)
Binance chain (BEP2)
Ethereum (ETH) (ERC-20) or (BEP-20)
TRON (TRX) or (TRC-20)
Zcash (ZEC)
We can add other protocols (and not only) at your request
Keylogger Live
- Full logging of bot keystrokes on any layout, including key modifiers such as Ctrl, Shift
Ability to set the frequency of receiving logs from the bot
Tasks (under development)
Ability to create tasks for bots based on rules
Other modules can be implemented at the request of the client
♕ Spyware installation for you takes up to 2 days, but usually it happens in 1.